Top Cybersecurity Trends 2022-2023:
16 experts share their predictions
The pandemic has altered the business landscape forever. Shifting teams from offices to a working from home model at such speed without the remote infrastructure in place presented many challenges, not least of which was the impact on cybersecurity. Two years in and cyberattacks have evolved to the point where hackers are able to craft higher volumes of sophisticated malware in less time than ever before, leaving SMEs extremely vulnerable. Despite this, as of 2022, just 43% of businesses operating in the UK have taken out insurance to safeguard against potential cyber-attacks. TWC IT Solutions, included among the top cybersecurity companies of 2021 and 2022, set out to understand the situation on the ground by interviewing sixteen business owners and industry leaders. In this article, we share what they believed to be the cybersecurity trends posing the highest risk for UK SMEs, plus their predictions for 2022 and beyond.
TABLE OF CONTENTS
Key Insights – The top Cybersecurity Trends of 2022-2023
> The Cybersecurity predictions of 16 industry experts
> Industry expert #1: Candid Wüest, VP Cyber Protection Research at Acronis
> Industry expert #2: David Stroud, Head of Europe & APAC at NanoLock Security
> Industry expert #3: Paolo Sartori, Managing Director of TWC IT Solutions
> Industry expert #4: Cindy Corpis, CEO of SearchPeopleFree.net
> Industry expert #5: Stephen Curry, CEO at CocoSign
> Industry expert #6: Marilyn Gaskell Founder & Hiring Manager of TruePeopleSearch
> Industry expert #7: William Westerlund, Co-Founder of Almvest
> Industry expert #8: Brian Kelso founder and CEO of BSK Data and Electricals PTY Ltd.
> Industry expert #9: Ernests Embutnieks, CEO and Founder of Wolf Of Desk
> Industry expert #10: Tom Okman, Co-founder & CEO at Nord Security
> Industry expert #11: Sarah Jameson, Marketing Director of Green Building Elements
> Industry expert #12: Isla Sibanda, Cybersecurity Specialist at Privacy Australia
> Industry expert #13: David Wurst, CEO of Webcitz
> Industry expert #14: David Attard, Digital consultant and web designer at CollectiveRay
> Industry expert #15: Gerrid Smith, CEO & Founder of Property Tax Loan Pros
> Industry expert #16: Edward Mellett, Co-Founder of Wikijob.uk
Key Insights – The top Cybersecurity Trends of 2022-2023
We compiled the top 5 list below after asking sixteen professionals and executives to share their insights and predictions for the coming year:
The top 5 cybersecurity trends of 2022:
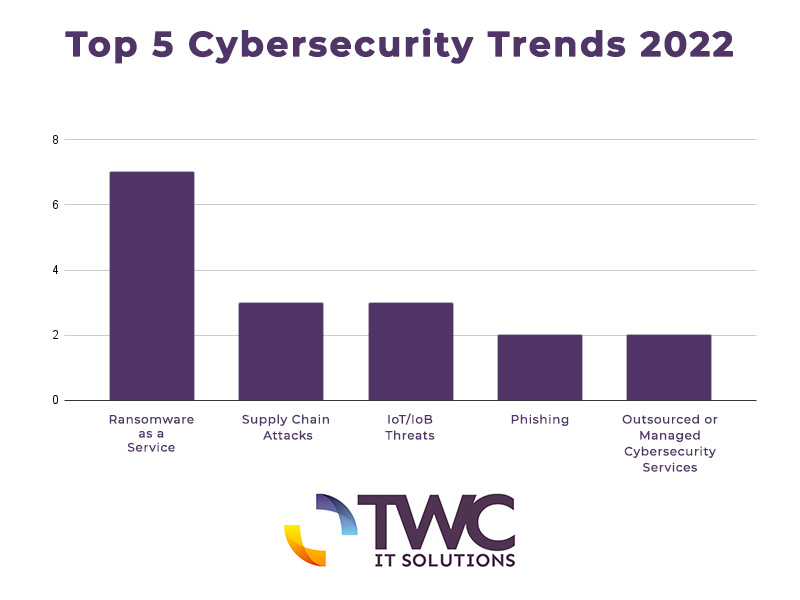
> Top Cybersecurity Trend #1: Ransomware as a Service (RaaS).
Most of the participants said they expect ransomware attacks to be much more targeted and dangerous this year, with the ‘Ransomware as a Service’ approach continuing to spread, putting many SMEs in danger of getting exposed.
> Top Cybersecurity Trend #2: Supply chain attacks.
Supply chain attacks enable a hacker to undermine distribution systems to deliver malware and access the networks of the supplier’s customers. Over the past year, many companies have opted to transition to Cloud architecture, which may offer additional routes for cyber criminals.
> Top Cybersecurity Trend #3: Internet of Things (IoT)/Internet of Behaviours (IoB) threats.
IoT exchanges and collects information, and the collected data, once analysed, provides valuable insight into customer behaviour, preferences, and interests (IoB). With the increasing number of connected devices, potential data leakage presents a growing concern for businesses as it can be easily exploited by hackers.
> Top Cybersecurity Trend #4: Phishing.
Phishing poses a high risk for businesses, as a malicious email or fake website can result in data and financial loss, damaged reputation, penalties, and intellectual property theft. Phishing attacks have increased 220% since the beginning of the pandemic, with hackers taking advantage of the vulnerabilities of the remote/hybrid working model.
> Top Cybersecurity Trend #5: Outsourced/Managed cybersecurity services.
With cyber crime reaching an all time high during the pandemic, companies of all sizes have realised they simply don’t have the expertise to hire an
in-house cybersecurity expert, so they need to invest in outsourced or managed cybersecurity services to protect their businesses.
Other emerging cybersecurity trends and key observations
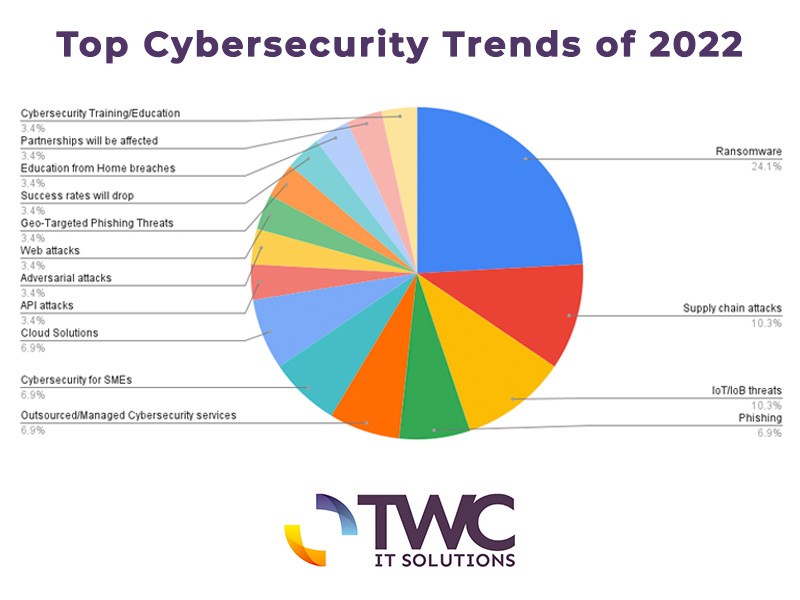
> 33% of the participants agreed that machine learning and AI will play a significant role throughout every aspect of business operations this year.
> 17% of the experts also agreed that the Internet of Things (IoT) will evolve, being one of the main targets for cyber attacks in the near future.
> Other rising trends we spotted were; cloud-based cybersecurity solutions, API attacks, adversarial attacks, web attacks, geo-targeted phishing threats, dropping of success rate, breaches in education from home, affected partnerships, cybersecurity training for personnel and SME focus in cybersecurity.
Discover more resources about cybersecurity
The Cybersecurity challenges every business needs to deal with in 2023
The Cybersecurity predictions of 16 industry experts
When you’re looking to understand market vibes, one of the most reliable sources is to ask industry experts. So that’s what we did – we asked sixteen experienced professionals, coming from eight different markets in total, to share their insights and predictions with us. Here’s what they said:
Industry expert #1: Candid Wüest, VP Cyber Protection Research at Acronis

“Ransomware will expand further to MacOS and Linux, as well as new environments such as virtual systems, cloud and OT/IoT.”
Ransomware
Ransomware is one of the most profitable cyberattacks at the moment. Despite some recent arrests, there is no end in sight. Ransomware will expand further to MacOS and Linux, as well as new environments such as virtual systems, cloud and OT/IoT. Anything that is connected to a reachable network is a potential target. This will increasingly lead to consequences and impacts in the real world, and thus also to more demand for official regulations and sanctions. Stealing data for double extortion as well as disabling security tools will be the norm, but it will also become more personal with insider threats and personal data. The chaos will continue as groups keep rebranding to defy investigations and Ransomware-as-a-Service will get smaller tier groups allowing for overlapping usage of different families.
Phishing
Malicious emails and phishing in all variations are still at an all-time high. Despite constant awareness campaigns, users still fall for them and enable the attacker to compromise their organisation. We don’t expect AI to fully take over phishing emails in 2022, but expect increased automation and personalised information from the various data breaches, making them more effective. New tricks against OAuth and MFA will continue to generate profit for attackers, allowing them to takeover accounts, despite plans from companies such as Google to auto-enrol 150 million users to 2FA. In order to bypass common anti-phishing tools, attacks such as business email compromise (BEC) will make use of alternative messaging services, like text messages, Slack or Teams chat.
Supply chain attacks
Attackers are going after the trusted connections that allow them to get into company networks. Software supply chain attacks are one of these methods, but even without full compromise of a vendor, there are similar ways in. Attackers are going after the management tools used by the administrators like professional services automation software (PSA) or remote monitoring and management (RMM) tools. They are the key to the kingdom, and the cybercriminals will use them against you. Service providers in particular will be targeted more frequently, as they often have many automation tools in place for efficient rollout of new software. Unfortunately, this is now being done by the attackers to distribute malware.
API attacks
Cloud services are booming and so are serverless computing, edge computing and API services. In combination with container orchestrations like Kubernetes, processes can be efficiently automated and dynamically adapted to the circumstances. Attackers are trying to disrupt this hyper automation by going after such APIs, which can seriously impact the business processes of a company.
Adversarial attacks in AI
As AI is more frequently used to detect anomalies in IT systems and automatically configure and protect any valuable assets, it is understandable that attackers increasingly will try to attack the logic within the AI model. Being successful and reversing the decisions inside the AI model can allow an attacker to remain undetected or generate a Denial of Service attack (DDoS) with an undesired state. It may also allow them to identify timing issues, whereas slow changes are not seen as anomalies and thus not blocked.
Return of the web attacks
Websites still make up an important part of the business Internet. We expect to see a rebirth of attacks against web servers. Attacks such as Formjacking, whereby a small JavaScript code is added to websites in order to steal passwords and payment card details, may reemerge after many companies have moved to cloud services. We will also see the occasional ransomware attack trying to encrypt database content through web services.
Industry expert #2: David Stroud, Head of Europe & APAC at NanoLock Security

“Ransomware is now more focused on highly targeted attacks designed to maximise ransom leverage per incident.”
Though data shows 2021 saw a decrease in the total number of ransomware attacks, the average remediation cost per incident more than doubled. This reflects the changing nature of ransomware which is now more focused on highly targeted attacks designed to maximise ransom leverage per incident. Perhaps nowhere is vast leverage more easily attained than in OT environments and industrial control systems (ICS), so it is our prediction that these targets are even more heavily besieged in 2022 than they were in 2021. These targets not only deploy a large number of unsophisticated (and heretofore under-protected) connected endpoints that make for easy intrusion, but they also provide a critical service to the communities they serve, meaning they cannot afford to stop service for very long. Soft targets with little leverage and immense importance are an ROI dream for hackers, so look for 2022 to include more examples like the Colonial Pipeline incident or the growing number of regional water treatment plant hacks.
Industry expert #3: Paolo Sartori, Managing Director of TWC IT Solutions

“SMEs need to urgently prioritise their cyber defence strategy to protect both their digital assets and their reputation.”
The cybersecurity trends of 2022 will definitely be influenced by the new hybrid working model. The cybersphere is becoming more advanced by the hour, but ransomware and phishing are also on the rise, and these are the types of attacks that can hit businesses hard. Over the pandemic, they’ve developed highly sophisticated ways to take advantage of the fragile state of some companies and extort financial resources. As such, SMEs need to urgently prioritise their cyber defence strategy to protect both their digital assets and their reputation. The last two years have shown just how vital preparation is for businesses navigating an uncharted future.
Industry expert #4: Cindy Corpis, CEO of SearchPeopleFree.net

Cindy Corpis,
CEO of SearchPeopleFree.net
![]()
“To restrict the impact of data thefts, losses, and breaches on customers, we may see a growing number of regulatory obligations placed on Chief Information Security Officers, similar to the responsibilities of Chief Financial Officers.”
Ransomware is becoming a bigger problem
According to the UK National Cyber Security Centre, ransomware assaults increased threefold in the first quarter of 2021 compared to the same period in 2019. According to PwC research, 61% of technology executives expect this to increase in 2022. We can once again attribute much of this to the internet and the increase in the amount of activity conducted online and in digital spaces.
Vulnerable Things on the Internet
By 2022, the internet of things (IoT) is expected to have grown to 18 billion linked devices. As a result, fraudsters seeking access to secure digital systems now have a much larger number of potential access points. The IoT will also be more advanced in 2022. Many companies are working on “digital twins,” which are detailed digital replicas of entire systems or even enterprises.
Risk is catching up to regulation
Security Magazine predicts that 2022 will be the year when regulators pull out all the stops to get a handle on the situation. As a result, sanctions that presently solely cover breaches and losses may be expanded to include vulnerabilities and exposure to prospective damage. Another factor could be the growing number of jurisdictions enacting legislation relating to ransomware payments. To restrict the impact of data thefts, losses, and breaches on customers, we may see a growing number of regulatory obligations placed on Chief Information Security Officers, similar to the responsibilities of Chief Financial Officers.
Industry expert #5: Stephen Curry, CEO at CocoSign

“To mitigate the risks to their business, SMEs need to adopt a proactive approach towards risk and security management.”
One of the key trends we will see in 2022 is the rise of cybersecurity for SMEs. Cybersecurity for SMEs refers to protection for small business owners against cyberattacks and data breaches, ensuring information security. Small and medium-sized businesses are increasingly at risk for cyber breaches, so it is important to assess their protection and access resources to mitigate the issue. At present, there are more than 3 million companies on SME-Online, the largest online marketplace for small enterprises and startups. Through this network of thousands of online platforms, new and established businesses can be connected nationally and globally. The rise in popularity of SMEs and startups on India’s e-commerce sites means that small businesses are now exposed to new risks from cyber-attacks. To mitigate the risks to their business, SMEs need to adopt a proactive approach towards risk and security management.
Industry expert #6: Marilyn Gaskell, Founder & Hiring Manager of TruePeopleSearch

Low-Code No-Code AI
Because there are so few data scientists available to fill roles on a global scale, low-code and no-code AI is one of the most democratic innovations to emerge in the business in years. In essence, this method to AI necessitates little to no programming, allowing anyone to “tailor apps to their needs using simple building pieces.” As a result, developing low-code and no-code AI solutions that enable businesses to compete without data professionals is critical to keeping sectors open and competitive.
The Rise of the Cloud
As a result of the Covid-19 pandemic, cloud computing has become one of the unavoidable data analysis advances in recent years. With more data to deal with than ever before, organisations worldwide have embraced cloud-based sharing and management of digital services. The rise of the cloud has more benefits than drawbacks, making it one of the important data analysis trends for creators to watch out for in the next few years. It can keep data secure, protect businesses from cyber-attacks, and boost scalability.
Industry expert #7: William Westerlund, Co-Founder of Almvest

“Small and medium-sized businesses have an easier time dealing with security alerts and a better understanding of the state of their overall security posture as a result.”
Human expertise assists with cyber security automation
Even the most advanced artificial intelligence or machine learning can’t be depended upon to discover indicators of compromise in cyber security, hence it’s best to use human intelligence (in a scalable fashion) in certain cases. This combination will be necessary for addressing vulnerabilities, reducing the threat surface, and preventing assaults efficiently.
Active or automatic blocking approaches, cross-correlation of pertinent telemetric data, risk-rated answers, and dashboards or portals with automated remediation procedures are some examples of this automated technology. Human involvement, on the other hand, is essential during decision-making processes but not always so during investigative ones. Automated systems must be supplemented with human control when new dangers emerge. Reduced false positives and tiredness will result from this. As a result, small and medium-sized businesses have an easier time dealing with security alerts and a better understanding of the state of their overall security posture as a result.
Industry expert #8: Brian Kelso, Founder and CEO of BSK Data and Electrical PTY Ltd.

“Since cybercriminals utilise further developed strategies to make professional business email compromise assaults (BEC), phishing messages and noxious URLs stay common on the web.”
Geo-Targeted Phishing Threats
Phishing assaults are presently the most inescapable security danger to the IT area, with many succumbing to phishing messages. Since cybercriminals utilise further developed strategies to make professional business email compromise assaults (BEC), phishing messages and noxious URLs stay common on the web, then again, actually they are currently exceptionally limited, more customised, and are geo-focused on.
AI
In online protection, the job of AI (ML) is developing and has now become more proactive. With ML, network safety becomes easier, more compelling, and, simultaneously, more affordable. From a rich dataset, ML creates designs and controls them with calculations. Along these lines, it can expect and react to dynamic assaults progressively.
Industry expert #9: Ernests Embutnieks, CEO and Founder of Wolf Of Desk

“Cyber security services will improve to better anticipate and combat potential threats in the near future.”
The growth of managed cyber security service choices
Cyber security requirements for small and medium-sized businesses necessitate the use of competent security professionals. When it comes to SMBs’ present demands, budget, and ability to adapt to changing conditions, Managed Service Providers (MSPs) or Managed Security Service Providers (MSSPs) can provide assistance. Customised solutions and shifting and evolving demands are well served by managed service options.
Cyber security services will improve to better anticipate and combat potential threats in the near future. When it comes to cyber security, many small and medium-sized businesses (SMEs) have started relying on external services to help them strengthen their defences. If an organisation’s level of protection is lacking, an assessment of its cyber security maturity is a useful tool. Prescriptive counsel and remediation activities are frequently included in these evaluations.
Industry expert #10: Tom Okman, Co-founder & CEO at Nord Security

“The forecasted retreat of the pandemic will lead a part of the workforce to return to the office or adapt a hybrid form of work instead of full WFH.”
The biggest stories in the industry in 2022
Hackers will focus their efforts on supply chain attacks. Following the two years of turmoil in supply chains across industries, cybercriminals will aim to capitalise on this intricate part of the global economy. The codependency of actors involved in the make-up of supply chains renders them a tempting target for cybercriminals. An attack on one company puts mounting pressure on several, increasing the chance of a ransom payout. That’s why recovering supply chains will become prime targets for cyberattacks in 2022.
The trends that will ascend/gain greater traction in 2022
The success rate of cyber attacks on businesses will decrease but still remain above the pre-pandemic levels. After two years of exponential growth in cyberattacks, predicting the opposite may seem counterintuitive. But security issues appeared on the radar for a lot of companies, possibly enough to compel many to invest in cybersecurity. The forecasted retreat of the pandemic will lead a part of the workforce to return to the office or adapt a hybrid form of work instead of full WFH. This will reduce potential access points for hackers. Meanwhile, those who opt for permanent remote work will have had the time to address the security issues overlooked in the rushed transition from offices.
Industry expert #11: Sarah Jameson, Marketing Director of Green Building Elements

“Organisations can use IoB to improve customer interactions, analyse consumer preferences, and make purchase decisions to stay competitive and maintain an edge over developing difficulties.”
Internet Of Behaviours
Businesses and organisations continue to rely more on information and data as a key to success as the world becomes more digital. The internet of behaviour, or IoB for short, is an important part of customer data. It gives useful information about consumer behaviour. Organisations can use IoB to improve customer interactions, analyse consumer preferences, and make purchase decisions to stay competitive and maintain an edge over developing difficulties.
In some ways, IoT is similar to the internet of things in that it provides greater insight into how consumers engage in the purchasing process. Furthermore, it entails psychological data analysis following data collection from IoT and various web sources, whether big data, BI or CDP. Overall, this new technology aims to assist businesses to improve user engagement and their clients’ experiences in more meaningful ways. Even though this technology is still in its early stages, analysts estimate that more than half of the world’s population has been exposed to at least one Internet of Things (IoT) initiative from private businesses or the government. This suggests that it could be one of the next technologies to go widespread in the next few years.
Industry expert #12: Isla Sibanda, Cybersecurity Specialist at Privacy Australia

Cybersecurity practices will become powered by Artificial Intelligence
Artificial intelligence shows immense promise when it comes to dealing with cybersecurity threats and coming up with advanced solutions. It can be used to counteract cybersecurity by identifying the patterns of behaviour that can be indicators of abnormalities. The thousands of data points that can be targeted by cybercriminals can be efficiently monitored using artificial intelligence features.
There will be an increase in Ransomware threats
The pandemic has recently opened up companies to more probabilities of attack as more work, hybrid work cultures, and third-party integrations became more common. There are expected to be three times more ransomware attacks in the coming year as the number of activities carried online increased significantly during Covid’19. Hackers have become more innovative with the way they carry out cyber-attacks which is why I believe companies need to become self-aware and invest in the latest software updates and devices to increase the level of data security.
Cyber-security risk and exposure will affect partnership decisions
As the saying goes, any cybersecurity link will only be as strong as its weakest link. This will cause organisations to become more cognisant about the level of security measures companies have in place when deciding to form partnerships. Furthermore, a collaboration between two organisations can be opening up the organisations to a vulnerability which is why I expect businesses will increasingly use cybersecurity resilience and exposure as a determining factor in deciding who they create business partnerships with.
Industry expert #13: David Wurst, Owner and CEO of Webcitz

Sensitisation of the User
With the severity of cybercrime increasing, some businesses have established measures to strengthen their organisation’s security, maintain a positive customer experience, and strike a balance between security and ease. To protect the company’s reputation, it is vital to educate consumers on spotting and preventing network attacks. Many people are unfamiliar with the tactics employed by cybercriminals.
As a result, it is vital to educate the public in order to prevent such assaults. Numerous businesses use the internet, visual aids, and traditional classroom methods to sell and train their personnel. Additionally, staff is trained on the proper handling and sharing of sensitive corporate information.
Industry expert #14: David Attard, Digital consultant and web designer at CollectiveRay

“By using artificial intelligence, companies can detect fraud and monitor unusual behaviour.”
Other than work from home, in what single way did COVID-19 change IT forever?
Though digital transformation has been on the up for a while, I think COVID may have been the final nail in the coffin for the physical document and analogue-led processes.
Whilst within our business we’ve been fortunate to be a few steps ahead in digitalising our business processes, a lot of companies haven’t been so lucky. Many have had their hand forced, and have had to take their documents and operations online much more quickly than they were expecting to.
Having documents online has been essential for organisations to share information and simply function as workforces have dispersed. How many employees have printed things out while they’ve been working from home? When your workers are mostly remote, access to physical documents is limited, and the need for hard copies disappears with no one to pass them along to. Gradually the last hold-outs to pen and paper are being converted.
What made this single change so momentous?
Print and paper have endured across almost all industries and geographies, in most cases, far longer than necessary. Despite increasing digitisation, people have clung on to the perceived safety and reassurance of the physical document for more generations than I care to count.
But COVID and home working may finally have quashed paper’s enduring legacy. In the current circumstances, the idea of ‘digital everything’ has prevailed as the only way forward for modern businesses and institutions.
Industry expert #15: Gerrid Smith, CEO & Founder of Property Tax Loan Pros

“Due to the increasing attack surface from less secure home working environments, ransomware attackers will target cloud and datacentre workloads.”
Supply chain assaults rise
Economic shortages and disruptions will allow malevolent actors to strong-arm targets for large rewards. AaaS agents will be particularly keen on gaining residence and selling it to the highest bidder. In the future, criminals may threaten to hold the victim’s crucial data, leak and publicise the breach, target their consumers, and attack their supply chain or partner vendors.
Modern ransomware
Ransomware wreaked havoc on organisations of all sizes in 2021. Small and medium-sized businesses (SMBs) were exploited by ransomware as a service (RaaS) gangs. Sadly, ransomware will continue to adapt and spread. The modern ransomware will grow more targeted and prevalent, and ransomware operators will employ more sophisticated extortion strategies including exfiltrating data to weaponise it. VPNs, spear-phishing emails, and open RDP ports will all remain targets, but we expect the cloud to grow in importance as more firms shift their data there. Due to the increasing attack surface from less secure home working environments, ransomware attackers will target cloud and datacentre workloads.
Industry expert #16: Edward Mellett, Co-Founder of Wikijob.uk

“Organisations can acquire elastic and scalable IT-related services at lower costs using cloud-native platforms.”
Cloud-Native Platform (CNPs)
The traditional office-based business model is giving way to hybrid and increasingly remote alternatives. As a result, data infrastructure must adapt to the current and future workplace’s geographically spread character. The change necessitates the use of distributed infrastructure and services, which are best offered in the cloud. As a result, it is extremely beneficial in a variety of digital activities, including the most recent mobile app development trends.
Organisations can acquire elastic and scalable IT-related services at lower costs using cloud-native platforms. Gartner predicts that by 2023, 75 percent of distributed businesses will outgrow non-distributed competitors by 25 percent. Meanwhile, forecasts show that by this year, CNPs will assist 95 percent of all digital efforts. Cloud-native platforms enable organisations to receive elastic and scalable IT-related services at lower costs, allowing them to fully utilise the benefits of cloud computing.

Boglárka Chamer
Social Media Executive, TWC IT Solutions





















0 Comments